What is the dark web?
Did you know that part of the internet is hidden? Known as the “dark web,” it is a part of the world wide web that requires special software to access. Once inside though, a whole new side of the internet is available for access.
The dark internet is a virtually anonymous place. It is a place where all kinds of illicit activities occur. This section of the web has been used as a place of choice for groups wanting to stay hidden online from governments and law enforcement agencies. It has also been used by pedophile groups, terrorists and criminals to keep their online affairs secret. Whistleblowers have used the dark internet as a place to communicate anonymously with journalists. Plus, it has been used as a dark marketplace.
Illegal products and services are regularly sold on the dark internet for profit. Some of the products sold include illegal drugs, firearms or even stolen identities. In its early days, these transactions were paid with Bitcoin. Nowadays, other more secure cryptocurrencies are gaining ground for dark internet transactions. This is making it hard for law enforcement to prevent these types of transactions.
How to get on the Dark Web
Getting on the dark internet is not incredibly difficult. One of the most popular and easy ways is to use a Tor browser.
Originally called “The Onion Router”, Tor browsers use onion routing technology developed by the United States Navy in the 1990s. This technology provides secrecy and anonymity to its users by disrupting messages passed through the Tor network to encrypt user IP addresses. The Navy originally created Tor as a way to gather open-source intelligence.
Over time, other users have begun using Tor technology. With increasing privacy concerns, Tor offers a way for people to use the internet anonymously and without their data being collected.
Tor users must be careful though. If a user accesses their social media accounts on a Tor browser, this has the potential to expose their identity. This is because usernames and email addresses can be traced back to source identities.
Why Identity Theft is so Common
As mentioned before, stolen identities are regularly sold for profit on the dark internet. This section of the web is the ideal place for criminal hackers to sell personally identifiable information (PII) from unassuming consumers.
In order to get started as an identity thief, a person can go to a marketplace in this subsect of the web to purchase resources and tools that will help them succeed. Packages such as “Ultimate Fraud Package—65000 items—2016 + FREE GIFT” contain everything a person would need to get started. Ebooks, Cryptocurrency Guides, Hacker Tutorials, Carding Guides, Cashout Tutorials and Anarchist Anarchist? Handbooks are all bundled into the previously mentioned package for a low price of $9.99. These types of packages make becoming an identity thief a low-cost investment with high rewards.

Ways Identity Information is Stolen
Personally identifiable information (PII) is most often stolen from individuals through data breaches. Data breaches have become more and more common over time, with the number of individuals affected increasingly yearly. In 2017 alone, over 16.7 million United States citizens were victims of identity theft. The amount of money stolen from them was upwards of $16.8 billion dollars.
One of the most common ways data breaches begin is through email spearphishing. If a hacker performs a successful attack, they can access everything within an organization’s network, including PII. For example, 143 million US consumers—nearly half of all Americans—were affected by the Equifax data breach in 2017. Hackers were able to access social security numbers, birthdates, addresses and driver’s license numbers from affected individuals.
The Cost of Identities on the Dark Web
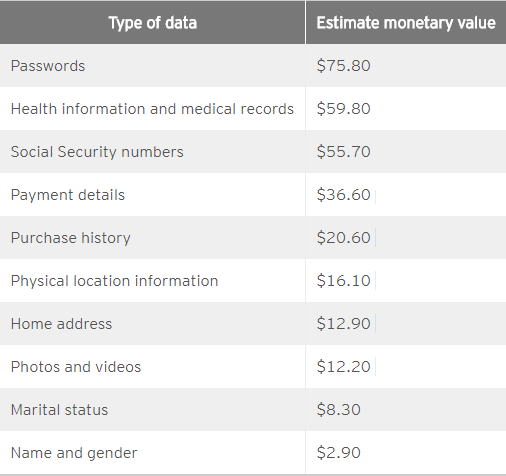
Surprisingly, buying PII is relatively cheap on the dark internet. Below are some of the most common types of PII sold on there along with their average price:
How to Protect your Identity
The United States government encourages consumers to protect themselves from identity theft in the following ways:
- Secure your Social Security number (SSN). Keep it in a safe place in your home away from where others can access it easily. Do not give out your SSN unless absolutely necessary. Always request that a company provide information about how they will keep your SSN safe and protected from data breaches if you must give it out.
- Do not respond to any unsolicited requests for your PII online, on the phone or by mail.
- Create complex passwords that identity thieves cannot easily guess. Change passwords promptly if you interact with any companies that announce a data breach.
- Install firewall and virus protection on your computer.
You can also follow these steps for your children to ensure their identities remain safe as well.
How Companies Can Help Protect Identities
Identity theft is becoming more common every day. With how easy it is to become a cyberhacker, identity theft can be expected to continue rising in the future. It is in a company’s best interest to prevent their databases from being breached. This ensures that they are protecting the PII of their users and preventing identity theft before it happens. In a world where data breaches are rising, taking steps to prevent them from happening will help businesses build positive relationships with their customers.
Furthermore, companies must come up with innovative ways to prevent the use of stolen PII in their systems. Doing this will make it more difficult for cybercriminals to use PII illegally. If the use of stolen identity information can be reduced, then the need to steal PII will decrease as well. This will help build trust with consumers by showing them that companies are taking an active interest to protect their identities.